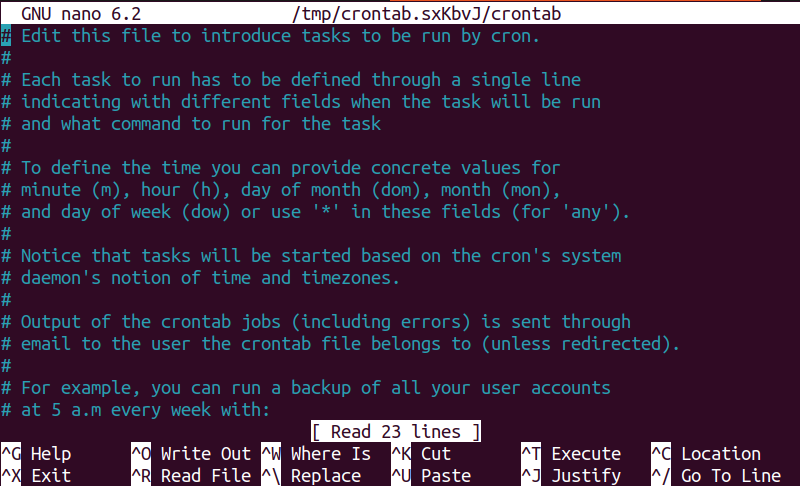
IPTABLES
Similar to tcpdump, the LOG target of iptables allows you to log each packet that’s sent to and from WireGuard. Most Linux systems use iptables, or its newer sibling nftables, to define their firewall.
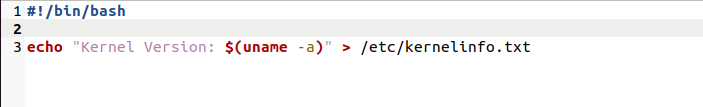
If you’re using iptables, you can run the following commands to add iptables rules that will log the header info of IPv4 packets carrying WireGuard encrypted content (where 51820 is the ListenPort in your WireGuard config):
If you’re using IPv6 networking, replace iptables with ip6tables; or if you’re using both IPv4 and IPv6, run both variants.
Once you do that, you’ll be able to see WireGuard packets logged to the kernel message buffer. If your system is set up with rsyslogd, journald, or a similar logging daemon, you can use it to see this logging. With rsyslogd, check the /var/log/kern.log or /var/log/messages file. With journald, run journalctl -ek.
To capture this logging to its own file, you can “tail” these messages via the dmesg command’s -w (follow) flag:
This will allow you to track the remote IP addresses that are connecting to your local WireGuard interface. A WireGuard handshake and short encrypted HTTP request and response will look like this:
In the above output, 198.51.100.1 is the IP address of the ethernet interface on the local host, and 203.0.113.2 is the IP address of the remote WireGuard endpoint (the remote endpoint is also listening on port 51820, but the above iptables rules would capture similar output even if the remote endpoint was on some other port).
You can also use iptables to log the packets that are sent inside the WireGuard tunnel. Run the following commands to log packet headers sent through the tunnel to and from the system itself (where wg0 is the name of your WireGuard interface):
And run the following commands to log packer headers sent through the tunnel to and from other hosts (if the system is operating as a router for other hosts on its network):
This will allow you to track exactly what is being sent through your WireGuard virtual private network. The short HTTP request and response from above will look like this when logging the packets within the tunnel:
In the above output, the IP address of local WireGuard interface is 10.0.0.1, and the IP address of the remote WireGuard peer is 10.0.0.2. An HTTP server is running on port 8080 of the local host, which the remote host is connecting to through the WireGuard tunnel (using the ephemeral TCP port 34770 inside the tunnel).
You can use the iptables logging on UDP port 51820 (the first example) to keep track of the external IP addresses that are connecting to your WireGuard network; and the iptables logging on the wg0 interface (the last example) to track which peers are using your network (and what they’re accessing inside the network).
You can remove iptables rules by running the same command you used to add them, except replacing the -I flag (or the -A flag for appended rules) with the -D flag. For example, you can remove the last two rules added above by running the following commands:
To check for active rules that you may want to remove, run iptables-save (iptables-save doesn’t actually save anything, it just dumps all active rules in a format that can be saved and restored).